OVERVIEW
In this particular tutorial, we are going to learn about the common DID Methods used by Ceramic. We will deep dive into each method by addressing their functionality, specification, and use cases.
All the relevant resources are provided at the end of the tutorial, make sure to check them out.
Ok now, before moving on let's just first understand the basics use case of Ceramic and Decentralized identity (DID).
What is Ceramic?
Ceramic is a decentralized network for composable data.
Ceramic makes building applications with composable Web3 data as easy as browsing a marketplace of data models, plugging them into your app, and storing, updating, and retrieving data from those models. When different applications reuse the same data models, their data is automatically interoperable. By decentralizing application databases, Ceramic makes data composable and reusable across all applications.
What is DID?
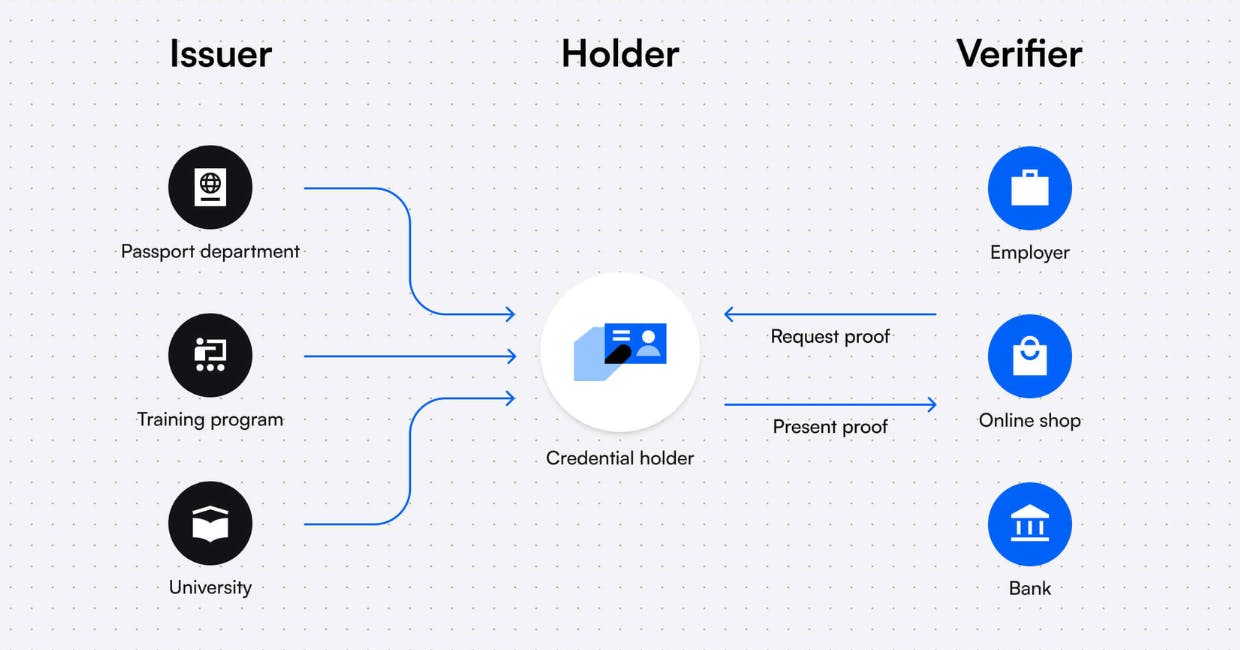 Decentralized identity (DID) is a type of identity management that allows people to control their own digital identity without depending on a specific service provider.
Decentralized identity (DID) is a type of identity management that allows people to control their own digital identity without depending on a specific service provider.
A digital identity is the body of information about an individual, organization, or electronic device that exists online. Data that form a digital identity include:
- User names and passwords
- Search History
- Social security number
- Buying history
INTRODUCTION
Let's understand What is DID Method?
DID methods are implementations of the DID specification. DID methods must specify a name for the method in the form of a string (see below), a description of where the DID document is stored (or how it is statically generated), and a DID resolver which can return a DID document given a URI that conforms to that particular DID method. There are over 40 DID methods on the W3C's official DID registry. Ceramic can support any DID method if needed, and currently supports the 3ID DID method and the Key DID method.
DID URIs look like this:
did:<method-name>:<method-specific-identifier>
DID Methods
- 3ID DID (CIP-79) - Recommended
- Key DID
- NFT DID (CIP-94) - In Experimental
- Safe DID (CIP-101) - In Experimental
1. 3ID DID (CIP-79)
 The 3ID DID Method (CIP-79) is a Ceramic-native account that can be used to authenticate to Ceramic to perform transactions on streams.
The 3ID DID Method (CIP-79) is a Ceramic-native account that can be used to authenticate to Ceramic to perform transactions on streams.
3ID DID Method Specification
3ID is a DID method that is implemented natively on Ceramic. It uses the Tile Document StreamType to create a mutable stream that stores the information which makes up the DID document for the 3ID. The Tile Document StreamType supports secure key rotation for 3IDs since its updates must be anchored into a blockchain, providing explicit versions and proof-of-publication at specific points in time (block heights). This means that 3ID inherits this property.
Use cases of 3ID DID Method
Multiple keys, secure rotations: The DID Document for the 3ID DID Method is implemented using a Ceramic Tile Document, making it fully mutable and able to support the secure addition and removal (rotation) of keys. This enables 3ID DIDs to handle multiple keys simultaneously and to remove keys when needed.
Support for blockchain wallets: When 3ID DIDs are used in conjunction with the Identity Index protocol (CIP-11) (using the 3ID Keychain definition (CIP-20)), a 3ID DID can be controlled from a user's existing blockchain wallets. This functionality is implemented by 3ID Connect.
Aggregated identities: 3ID DIDs can serve as a cross-chain identifier which can be controlled by all of a user's blockchain and Web3 accounts from any L1 or L2 protocol. This provides a way to unify a user's identity across all other platforms.
Great for end users: Due to all of the reasons above
2. Key DID
 The Key DID Method is an account that can be used to authenticate to Ceramic to perform transactions on streams.
The Key DID Method is an account that can be used to authenticate to Ceramic to perform transactions on streams.
The Key DID Method is the most simple DID method. It simply encodes a public key in the DID string, and when resolved converts this public key into a DID Document. Key DID is on the W3C's official DID method registry and is fully compliant with decentralized identity standards. Carefully read the considerations below before deciding to use the Key DID Method in your project.
Key DID Method Specification
For the full specification, see Key DID Method specification →.
Use cases of Key DID
The Key DID Method is only suitable for advanced users who will only want to ever use one keypair to control their DID, and who have strong key security practices - such as a developer - and so generally will not be appropriate for identities for non-technical end users.
3. NFT DID Method (CIP-94)
 The NFT DID Method (CIP-94) is an account that can perform transactions on streams. NFT DID accounts are controlled by the current owner of an NFT (non-fungible token).
The NFT DID Method (CIP-94) is an account that can perform transactions on streams. NFT DID accounts are controlled by the current owner of an NFT (non-fungible token).
NFT DIDs are still very experimental, so use them at your own risk.
NFT DID Method Specification
The NFT DID Method converts any non-fungible token on any blockchain into a decentralized identifier where the owner of the NFT is the controller of the DID. This is achieved by using the Chain Agnostic Improvement Proposals to describe NFT assets and blockchain accounts, as well as the Ceramic network to find the DID associated with the owner of the NFT.
Use cases of NFT DID
Extensible, mutable NFT metadata – NFTs currently have fixed metadata that is created when the token is minted. But what if we want an NFT to be able to collect data over time? With NFT DID, an NFT owner can annotate an NFT with additional information that is modified over time, such as a social graph for the NFT, a story behind the artefact, owner-restricted content, or, for example, a carbon offsetting certificate.
4. Gnosis Safe DID
 The Gnosis Safe DID Method (CIP-101) is an account that can perform transactions on streams. Safe DID accounts are controlled by the current members of a Gnosis Safe smart contract. Safe DID is on the W3C's official DID method registry and is fully compliant with decentralized identity standards, however they are still highly experimental, so use them at your own risk.
The Gnosis Safe DID Method (CIP-101) is an account that can perform transactions on streams. Safe DID accounts are controlled by the current members of a Gnosis Safe smart contract. Safe DID is on the W3C's official DID method registry and is fully compliant with decentralized identity standards, however they are still highly experimental, so use them at your own risk.
The Safe DID Method turns every Gnosis Safe contract into a Ceramic account capable of sending transactions to streams on Ceramic. It is similar in design and usage to the NFT DID account method.
Write permissions for streams whose controller is set to a Safe DID are restricted to the DIDs of the blockchain accounts that control the Gnosis Safe contract. When Gnosis Safe controller permissions change on-chain, so do the write permissions to streams owned by the Safe.
Gnosis Safe DID Method Specification
The Safe DID Method converts any instance of the Gnosis Safe smart contract system, deployed on any blockchain, into a DID. The list of owners from the OwnerManager.sol module gets converted into a list of controller DIDs in the resolved DID document. This is achieved by using the Chain Agnostic Improvement Proposals to describe the smart contract address, as well as the Ceramic network to find the DID associated with the owners of the Safe contract.
Use cases of Safe DID
- Security Requirements
The Safe DID derives most of its security properties from the blockchain which the given contract lives on and the Ceramic protocol. The security of different blockchains may vary so implementers may choose to limit their implementations to specific EVM-based chains. Ceramic most notably provides censorship resistance, decentralization, and requiring a minimal amount of data to be synced to completely verify the integrity of the caip10-links used to find the controller DIDs. For more details see the Ceramic specification.
- Privacy Requirements
The Safe DID utilizes a few components. First, blockchains provide a public, immutable audit trail of all previous owners of a Safe contract; these owners are blockchain accounts. Second, the caip10-link document on Ceramic similarly provides an audit trail for which DID a specified blockchain account has linked over time. The combination of these two proofs allows the Safe DID to permissionless create pubic mappings from a Safe DID -> blockchain accounts (owners) -> DIDs (owners). This allows the Ceramic protocol to enforce decentralized access control permissions that only allow the current owners of the Safe contract to make updates to content or resources owned by the Safe DID.
- Encrypting data to all Safe owners
A desirable feature of a DID method for the Gnosis Safe contract is that one can encrypt data for all the owners of the Safe. This can be achieved by first resolving the did:safe, then resolving all the controller DIDs. Once we have these we can retrieve the public encryption key (key exchange key) from these DIDs.
CONCLUTION
 Finally, we complete the deep dive into DID Methods.
As mentioned before these are the common DID methods used by ceramic. Ceramic can support any DID method if needed, and currently supports the 3ID DID method and the Key DID method. NFT DID Method (CIP-94) & Safe DID are still in the experimental phase, so use them at your own risk.
Finally, we complete the deep dive into DID Methods.
As mentioned before these are the common DID methods used by ceramic. Ceramic can support any DID method if needed, and currently supports the 3ID DID method and the Key DID method. NFT DID Method (CIP-94) & Safe DID are still in the experimental phase, so use them at your own risk.
